今天继续关于威胁情报的专题。威胁情报的理念,目前在国外已广为接受,最近美国也已将网络威胁情报信息共享视作提升其联邦政府信息系统安全的必要手段之一,并且发布了NIST SP 800-150 网路威胁信息共享指南草稿。
NIST SP 800-150 是 NIST SP 800-61 计算机安全事件响应指南的扩充,将信息共享、协调、协同扩展至事件响应的全生命期中。
本文对其主要部分进行摘录,更多内容可参照NIST发布的文档。
事件协同和信息共享的全生命期包括:
■Creation or Collection
■Processing
■Dissemination
■Use
■Storage
■Disposition
信息共享和协同的收益包括:
■Shared Situational Awareness
■Enhanced Threat Understanding.
■Knowledge Maturation
■Greater Defensive Agility
■Improved Decision Making
■Efficient Handling of Information Requests
■Rapid Notifications
协同和共享的挑战主要是:
■Legal and Organizational Restrictions
■Risk of Disclosure
■Preserving Privacy
■Producing Information
■Consuming Information
■Interoperability
■Classification of Information
■Establishing Trust
其认为的网络攻击生命期包括:
Phase 1—Reconnaissance
Phase 2—Weaponize
Phase 3—Deliver
Phase 4—Exploit
Phase 5—Install
Phase 6—Command and Control
Phase 7—Act on Objectives
.png)
威胁情报应具备的特征包括:
■Timely
■Relevant
■Accurate
■Specific
■Actionable
信息共享的架构包括集中式和P2P式:
.png)
其规划的美国国家联邦政府星型分层级的事件报告机制如下图:
.png)
其规划的美国国家信息共享和分析中心ISAC星型事件报告模型如下图:

美国国家信息共享流程如下图:
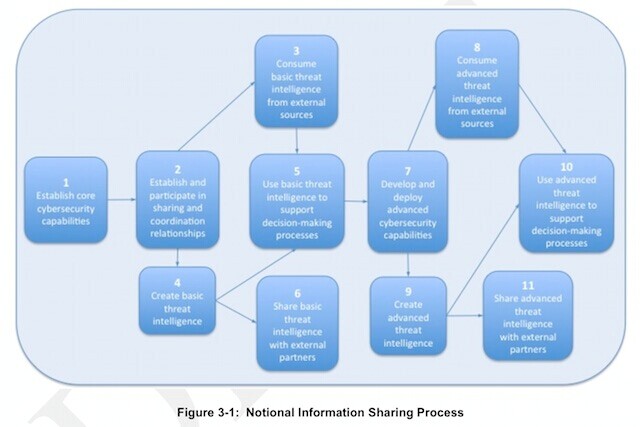
1.Establish core cybersecurity capabilities
2.Establish and participate in sharing and coordination relationships
3.Consume basic threat intelligence from external sources
4.Create basic threat intelligence
5.Use basic threat intelligence to support decision-making processes
6.Share basic threat intelligence with external partners
7.Develop and deploy advanced cybersecurity capabilities
8.Consume advanced threat intelligence from external sources
9.Create advanced threat intelligence
10.Use advanced threat intelligence to support decision-making processes
11.Share advanced threat intelligence with external partners
事件协同和信息共享组织应具备基础架构能力包括:
■Organizational Structure for Incident Coordination
■Asset, Vulnerability and Configuration Management
■Log and Alert Collection
■Log and Alert Search and Retrieval
■Response Tools
组织应具有的核心网络安全能力包括:
■Deploy, configure, monitor, and update sensors
■Manage log data
■Document, prioritize, and manage incidents
■Perform basic network traffic forensics
■Coordinate with system/information owners
部分可进阶具备的高级网络安全能力包括:
■Conduct “deep dive” digital forensics analysis of a compromise
■Actively collect, produce, use, and share threat intelligence
■Develop threat intelligence that reveals an adversary’s TTPs, behaviors, and motives
■Use knowledge management practices to enrich data, mature knowledge, and inform cybersecurity decision-making
信息共享的能力包括:
■Coordinate the exchange of threat intelligence
■Appropriately handle sensitive or classified information
■Normalize or transform information
■Ingest information from external threat intelligence sources
■Produce and publish threat intelligence
■Acquire actionable threat intelligence
事件响应全生命期:
.png)
用来共享的信息,可以是结构化数据、可机读数据(XML,CSV,JSON),也可以是未预先定义格式的非结构化数据。
典型的共享的信息内容包括以下类型:
■IP addresses and domain names
■URLs involved with attacks
■Simple Mail Transport Protocol (SMTP) headers, email addresses, subject lines, and contents of emails used in phishing attacks
■Malware samples and artifacts
■Adversary Tactics, Techniques, and Procedures (and effectiveness)
■Response and mitigation strategies
■Exploit code
■Intrusion signatures or patterns
■Packet captures of attack traffic
■NetFlow data
■Malware analysis reports
■Campaign/actor analyses
■Disk and memory images
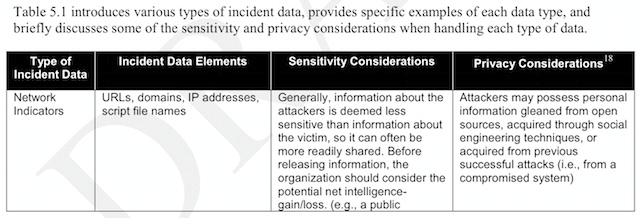
其也提到了,在信息共享的时候必须建立起规则,其首要需要注意的就是共享信息中的隐私问题:
.jpg)
信息的敏感性也至关重要,需要遵从谅解备忘录MOUs、保密协议NDAs或其他协议框架,同事也需要遵从PII、SOX、PCI DSS、HIPPA、FISMA、GLBA等法律法规。
同时也必须对交换的信息进行标识,约定其使用范围,典型标示包括:
■For Official Use Only
■Distribution limited to first responders
■Investigation underway, do not perform queries or active reconnaissance against these indicators
|